TEST YOUR KNOWLEDGE and take the phish test!
CLICK HERE TO SEE THE LATEST PHISHING ATTEMPT EXAMPLES
What is phishing?
Phishing is a cyber attack that uses disguised email as a weapon. The goal is to trick the email recipient into believing that the message is something they want or need — a request from their bank, for instance, or a note from someone in their company — and to click a link or download an attachment.
What really distinguishes phishing is the form the message takes: the attackers masquerade as a trusted entity of some kind, often a real or plausibly real person, or a company the victim might do business with. It's one of the oldest types of cyberattacks, dating back to the 1990s, and it's still one of the most widespread and pernicious, with phishing messages and techniques becoming increasingly sophisticated.
An email is likely a phish attempt if:
- The email, text, or voicemail is requesting that you update/fill in personal information. This is especially dubious if it’s coming from a bank or the IRS. Treat any communication asking for your credentials with extra caution.
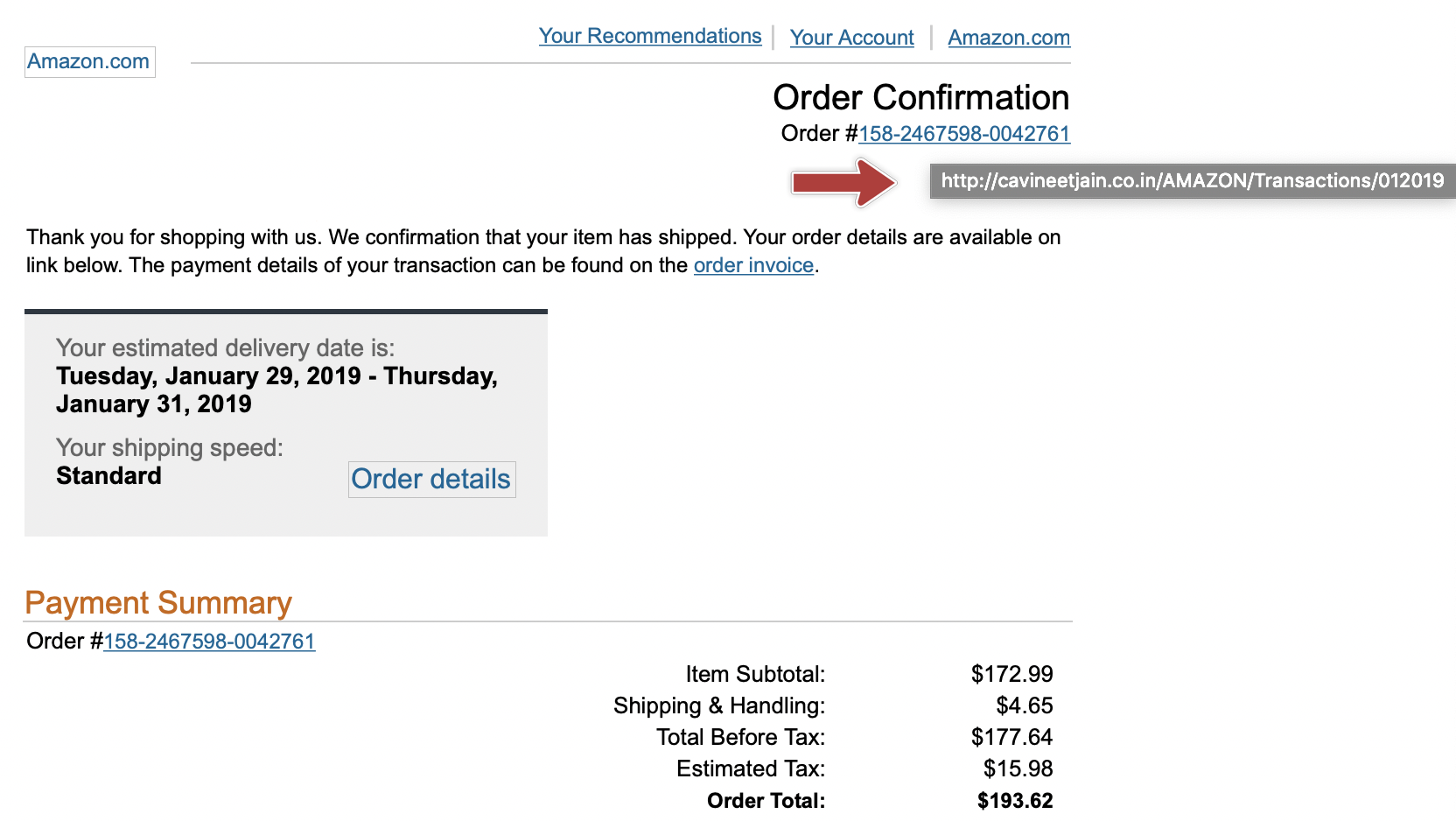
- The URL shown on the email and the URL that displays when you hover over the link are different from one another. See the image below for an example from an 'Amazon phish':
- The “From” address is an imitation of a legitimate address, especially from a business.
- The formatting and design are different from what you usually receive from an organization. Maybe the logo looks pixelated or the buttons are different colors. Or possibly there are odd paragraph breaks or extra spaces between words. If the email appears sloppy, start making the squinty “this looks suspect” face.
- The content is badly written. Are there obvious grammar errors? Is there awkward sentence structure, like perhaps it was written by a computer program? Take a closer look.
- A phishing email almost always sounds desperate. Whether they’re claiming that your account will be closed, an urgent request is needed, or your account has been compromised, think twice before double-clicking that link or downloading that attachment.
- The email contains attachments from unknown sources that you were not expecting. Don’t open them, plain and simple. They might contain malware that could infect your system.
- The website is not secure. If you do go ahead and click on the link of an email to fill out personal information, be sure you see the “https” abbreviation as well as the lock symbol at the beginning of the URL. If not, that means any data you submit is vulnerable to cybercriminals.
What should you do if you suspect an email is a phish attempt?
- Do not open attachments, click on URLs, or provide any information!
- Submit it to the IT department via this help site by Starting a Conversation.
- Delete it!
CLICK HERE to TEST YOUR KNOWLEDGE and take the phish test!
MORE READING AND MORE EXAMPLES:
Check the sender.
Sometimes, cybercriminals will fake (or "spoof") the sender of an email. If the "from" address doesn't match the alleged sender of the email, or if it doesn't make sense in the context of the email, something may be phishy.
- An email claims to come from the University, but it's from "udel@yahoo.com" instead of an "@udel.edu" address.
- An email claims to come from your friend John Doe, but the sender is "james@faceb00k.biz."
Check for (in)sanity.
Many typical phishing emails are mass-produced by hackers using templates or generic messages. While sophisticated attacks may use more convincing fake emails, scammers looking to hit as many different inboxes as possible may send out large numbers of mismatched and badly written emails. If the email's content is nonsensical or doesn't match the subject, something may be phishy.
- An email has the subject "Important documents," but the message itself is about your email account running out of storage.
- An email has a generic subject like "warning" or "FYI" and the message is a request for you to enter personal information or click on a suspicious link.
- An email contains a 2FA code that you did not request.
Check the salutation.
Many business and commercial emails from legitimate organizations will be addressed to you by name. If an email claims to come from an organization you know but has a generic salutation, something may be phishy.
- An email claiming to come from the University is addressed "Dear webmail user" instead of "Dear Jane Doe."
- An email claiming to come from one of your favorite stores is addressed "Dear customer," but the store's emails are normally addressed "Dear John Doe."
Check the links.
A large number of phishing emails try to get victims to click on links to malicious websites in order to steal data or download malware. Always verify that link addresses are spelled correctly, and hover your mouse over a link to check its true destination. Beware of shortened links like http://bit.ly, http://goog.le, and http://tinyurl.com. Additionally, a site using https:// (with a green padlock icon) should not be automatically trusted. You should not visit a website if your browser warns you about dangerous or deceptive content. If an email links to a suspicious website, something may be phishy.
- An email tells you to click on a link to "udel.com/passwordreset" to reset your password, but you were expecting a link to a "udel.edu" address.
- When hovering over a link to "barnesandnoble.com," you notice that the link actually goes to "barnsandmoble.com."
Don't let them scare you.
Cyber criminals may use threats or a false sense of urgency to trick you into acting without thinking. If an email threatens you with consequences for not doing something immediately, something may be phishy.
- An email warns, "confirm your account password or your account will be shut down."
- An email promises a reward to the first 100 takers and urges you to "click now to claim your prize."
- An email tells you to pay the attached "invoice" or "face legal action."
Don't give up personal data.
Some phishing emails will ask for your sensitive personal data, such as your account password or your Social Security number. Legitimate organizations will not ask you to provide this information over email. If an email demands sensitive information, something may be phishy.
- An email asks you to verify your account by typing in your username and password.
- An email asks you to provide W-2s, tax information, or other personal documents.
Don't open suspicious attachments.
Some phishing emails try to get you to open an attached file. These attachments often contain malware that will infect your device; if you open them, you could be giving hackers access to your data or control of your device. If you get an unexpected or suspicious attachment in an email, something may be phishy.
- An email instructs you to open the attached "court summons," but you aren't expecting a summons and you know that such a document would be delivered in paper.
- An email tries to deliver an attached "invoice" for your "recent purchase."
Check for poor spelling and grammar.
Typically, official emails from organizations you trust will not be rife with spelling and grammar errors. If an email claims to come from a legitimate organization but contains numerous errors, something may be phishy.
- An email reads, "Click to verify now you're account."
- An email claims to come from the "Univercity of Deloware" and asks you to "open imporant document imediately."
Don't believe names and logos alone.
With the rise in spear phishing, cybercriminals may include real names, logos, and other information in their emails to more convincingly impersonate an individual or group that you trust. Just because an email contains a name or logo you recognize doesn't mean that it's trustworthy. If an email misuses logos or names, or contains made-up names, something may be phishy.
- An email includes the UD logo, but it makes a suspicious request for your account information.
- An email claims to come from your bank, but uses an old logo.
- An email claims to come from the dean of your college, but the sender is a "hotmail.com" address.
If you still aren't sure, verify!
If you think a message could be legitimate, but you aren't sure, try verifying it. Contact the alleged sender separately (e.g., by phone) to ask about the message. If you received an email instructing you to check your account settings or perform some similar action, go to your account page separately to check for notices or settings (e.g., log in to Facebook and navigate to your settings instead of opening a suspicious-looking link that claims to go to your account page).
- You get a request from a coworker for files that person doesn't normally use, so you walk to her office to check whether she really sent the request.
- An unexpected email claiming to come from a social media site tells you that you need to change the password to your account. Instead of following the password reset link in the email, you open the site in a new browser tab and manually log in to check your settings.
More information is available at the following resources:
Avoiding Social Engineering and Phishing Attacks (US-CERT)
Explains what phishing is and offers tips for avoiding becoming a victim.
Phishing (OnGuard Online)
Explains briefly how to deal with phishing scams, including how to avoid them and how to report them.
Phishing scams (About.com)
Provides examples of common phishing scams and how to spot them.
How can I verify if an email is legitimate?
If you aren't sure whether an email is be legitimate, contact the alleged sender through a separate channel, such as over the phone or in person. If the email you received claims to come from an organization, look for that organization's official contact information.
If you want to verify whether a link is legitimate, hover your mouse over the link text and check its true destination. In many web browsers, a link's destination will appear in the lower left corner of the window. Watch out for spelling mistakes, missing or extra dashes, and fake domains (such as "udel.edu.com"). Your device won't know the difference between a legitimate link and a malicious one!
If you get an email stating that you need to log in to update or verify your settings, review information related to your account, or confirm something, it's recommended that you log in to your account the same way you normally would—don't follow links in a suspicious email. Use official login pages on the organization's real website.
Jed Krisch
Comments