To further assist with the proper handling of sensitive data, we provide an encrypted file system available to key members of each Lab at the FBRI.
The intent of this encrypted (at rest) file system is to store sensitive data such as participant records, spreadsheets, participant keys, etc. and provide an additional layer of protection that is separate from the main Lab Shares.
Access will be limited and the intent is not to store all research data in this space.
As with all FBRI on-line storage, all file activity taking place on the encrypted storage is captured, logged, and audited.
ACCESSING THE ENCRYPTED FILE SYSTEM:
NOTE: You will need to be connected to the FBRI wired network or FBRI VPN to access these resources.
- The Windows UNC path will be \\fileservices.vtc.vt.edu\efs\labname
- The OS X / Mac path will be smb://fileservices.vtc.vt.edu/efs/labname
Please note all the details below:
- Initially, until requested otherwise, only Lab Managers and PI’s will have access to the share. Start a Conversation with us if you wish to add additional staff.
- On FBRI Windows machines, the share will be automatically mapped to drive X:
- Encrypted file shares must be connected via SMB as NFS is not supported.
Encryption Specific Details:
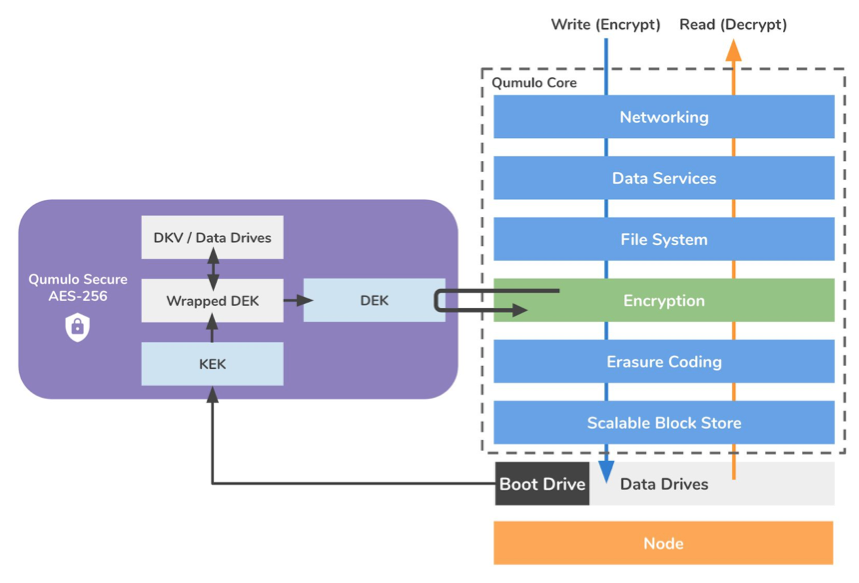
Our storage platform builds its implementation of encryption on rigorous AES-256 bit security standards expected of the enterprise. To boost performance and security, the platform leverages the AES-NI extension to the x86 instruction set on each node's CPUs. Encryption is done at the block level below the file system as shown in Figure 1 below, where all data and metadata to be encrypted, including the encryption keys themselves, are sent through the cryptographic module.
Software-based encryption encrypts the data using a two-key system for added security. A Key Encrypting Key (KEK) and the Data Encrypting Key (DEK). The KEK wraps the DEK which means that in order to decrypt the DEK and encrypt/decrypt data, you must first have the KEK.
Figure 1. This diagram shows the life of a write and read when being encrypted/decrypted on our encrypted file data platform.
PLEASE NOTE: Data stored on the network is backed up and protected. FBRI does not backup or protect data stored locally on workstations. All data accessed and associated file and folder operations taking place on FBRI network storage is captured in logs residing on a central logging facility.
REQUESTING ACCESS: An on-line access request is required to add / remove people from network shares. All access requests must be submitted by authorized personnel.
Jed Krisch
Comments